Secure Digital Future
Protect your organization's digital assets with our cutting-edge cybersecurity engineering and assessment and authorization services. Our expert team assesses vulnerabilities, designs and implements robust security protocols, and ensures compliance with industry standards. With our comprehensive approach, you can safeguard sensitive information, mitigate risks, and maintain trust in an ever-evolving threat landscape.
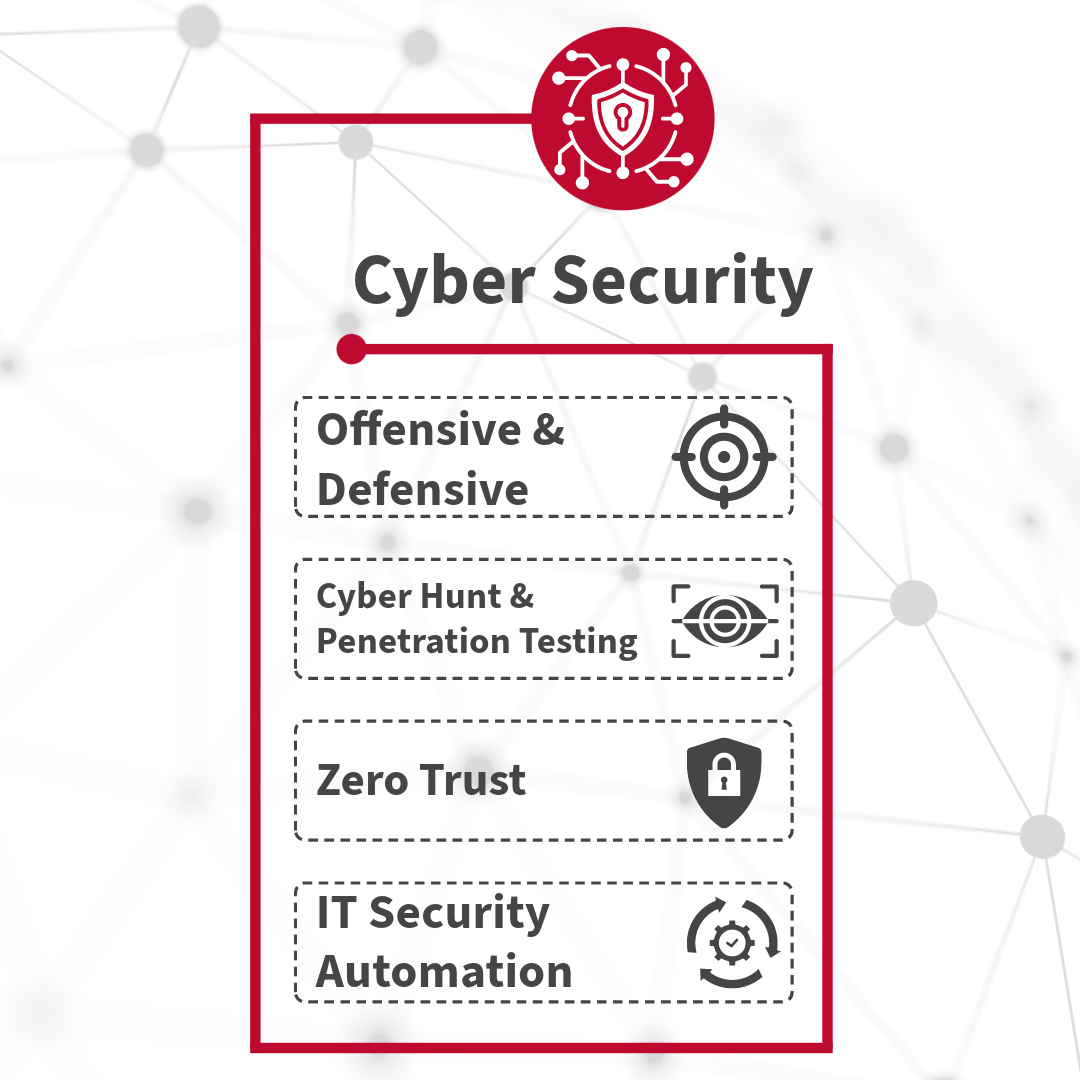
Cybersecurity
Empower your organization’s cyber defense with Base-2’s comprehensive approach. From proactive
penetration testing to thorough threat detection systems, we ensure your digital assets remain secure
against emergent Insider and State Actor threats. With continuous monitoring and expert incident
response, trust us to protect your agency's digital future.
Stay ahead of cyber threats with Base-2’s proactive and tailored approach. We perform regular cyber
hunt operations and penetration testing to identify and neutralize advanced threats before they
strike. With integrated threat intelligence and advanced analytics, our solutions empower our
customers to strengthen their cybersecurity posture and protect against evolving and emerging threats,
ensuring peace of mind in today's digital landscape.
Through stringent access controls, next-generation encryption capabilities, and continuous monitoring,
Base-2 ensures the strongest protection against Insider and State Actor threats. With our solid
encryption and segmentation techniques, rest assured your agency's digital assets are shielded against
evolving threats.
Base-2’s comprehensive automation frameworks streamline routine security tasks, ensuring unparalleled
efficiency and responsiveness in safeguarding digital assets. By integrating automation with advanced
threat intelligence and security analytics, trust us to proactively detect and mitigate threats,
keeping your agency ahead of evolving cyber risks.
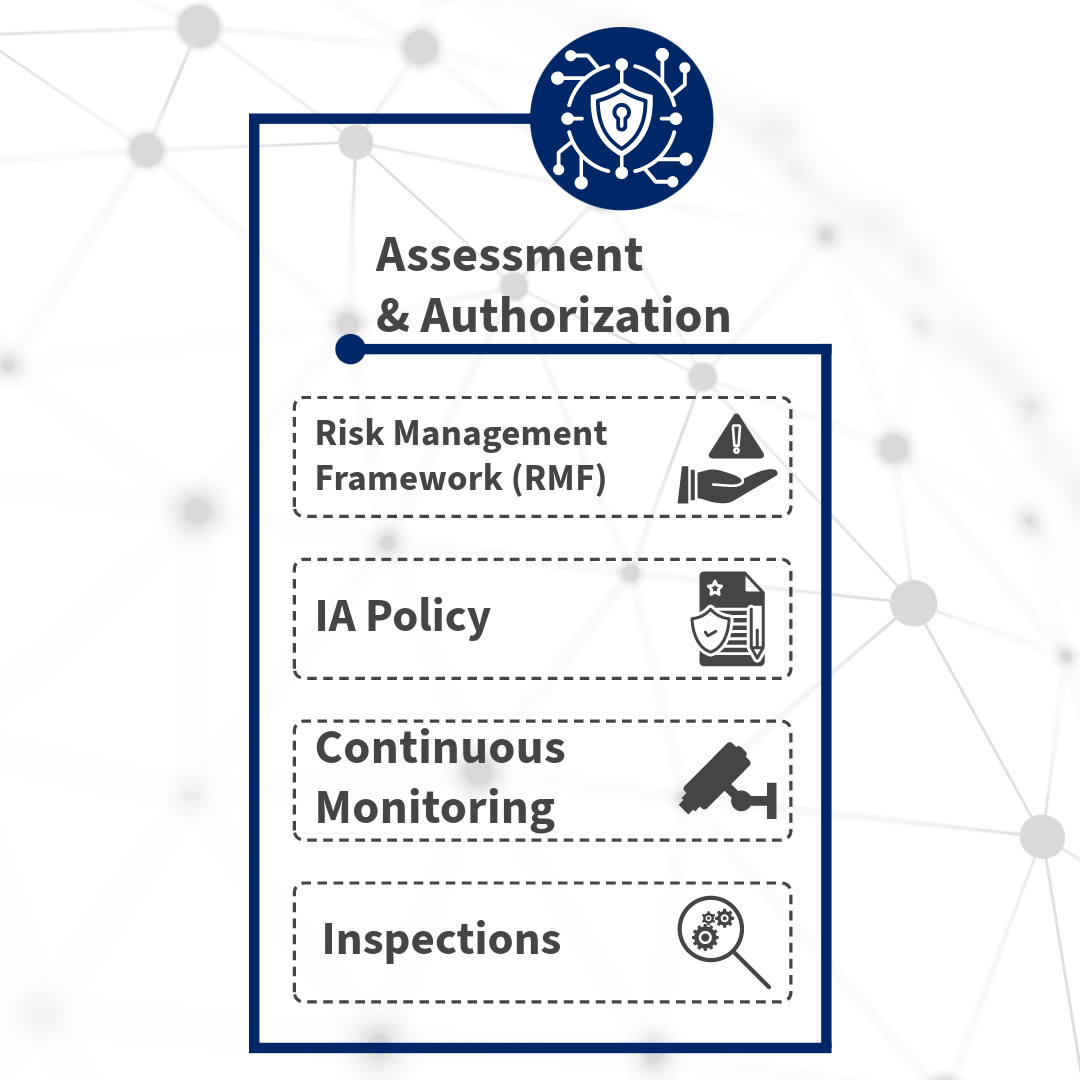
Assessment & Authorization
Base-2’s streamlined approach ensures certification and accreditation through specialized roles,
standardized documentation, and cutting-edge automation tools. With collaborative efforts and
proactive risk assessments, we ensure compliance with government regulations while reinforcing system
security.
Base-2 proudly offers custom-tailored Information Assurance Policy solutions. Aligned with industry
standards like NIST Special Publication 800-53, our comprehensive strategies bolster security,
mitigate risks, and ensure compliance. Seamlessly integrated into the A&A process, our solutions
empower government agencies to protect sensitive data and infrastructure with confidence.
Empower your security posture with Base-2’s innovative continuous monitoring solutions. We leverage
advanced tools track system activities and network traffic in real-time, ensuring proactive threat
detection and swift incident response. Our integrated threat intelligence feeds and state-of-the-art
security analytics allow customers to stay ahead of evolving threats while maintaining compliance with
government regulations. With our solutions, your organization can confidently solidify its security
posture and safeguard mission-critical operations against emerging threats.
Base-2 takes inspections very seriously. We establish clear criteria and protocols to ensure
compliance with security controls and regulatory requirements. Our team members’ strong attention to
detail enforces accuracy in evaluating system configurations and security posture.