Protecting Your Mission Priorities
Revolutionize your organization's security posture with our cutting-edge Zero Trust capabilities. Embracing a proactive approach, our solution ensures that no entity, whether internal or external, is inherently trusted, mitigating the risk of cyber threats and unauthorized access. By implementing continuous authentication, least privilege access, and robust monitoring, our Zero Trust framework empowers your business to navigate today's dynamic threat landscape with confidence, safeguarding critical assets and maintaining a secure digital environment.
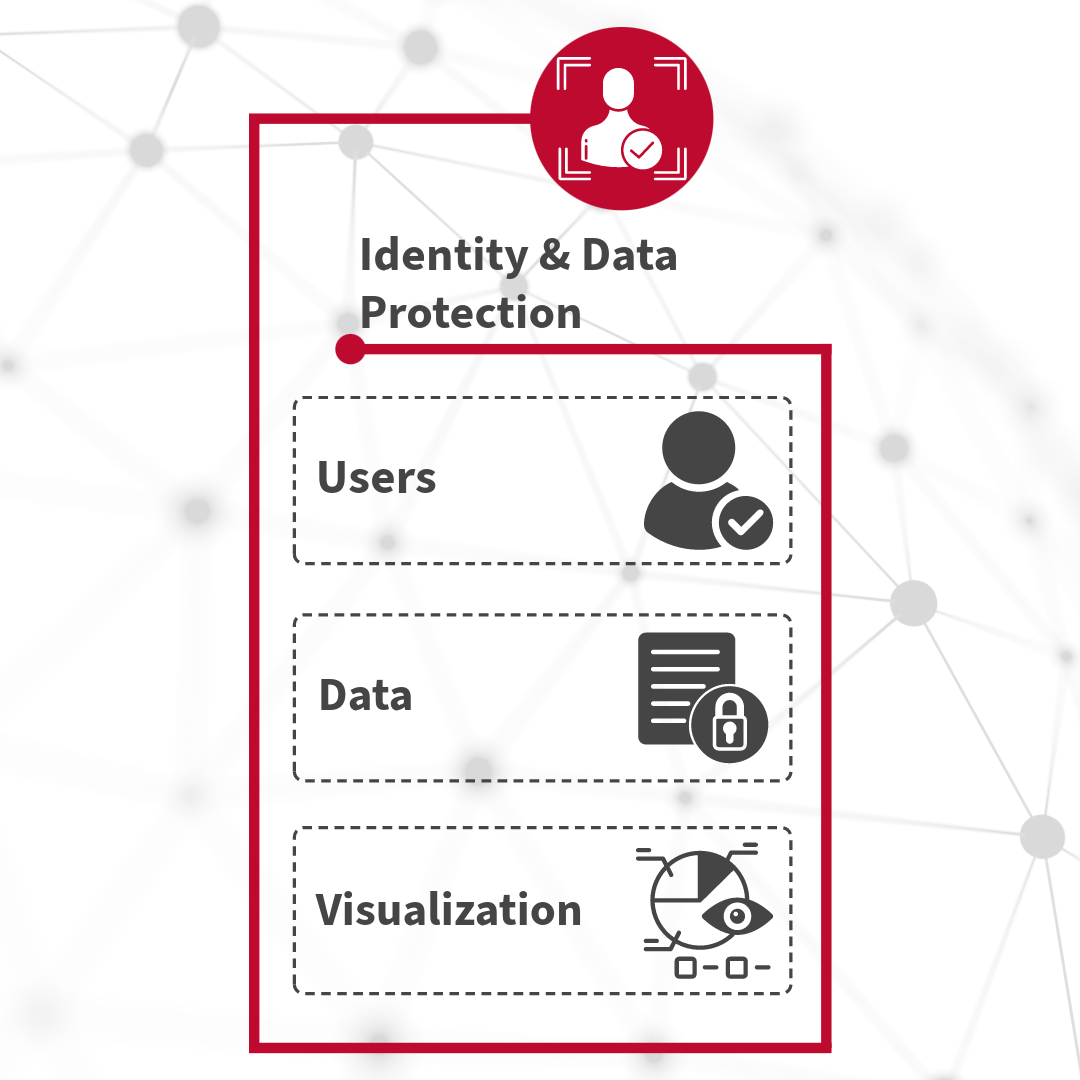
Identity & Data Protection
Base-2’s Zero Trust solution focuses on authenticating and verifying the identity of users attempting
to access resources within the network, regardless of their location or device. It emphasizes the
principle of least privilege, granting users only the necessary access permissions based on their role
and context. Additionally, continuous monitoring and adaptive authentication techniques are employed
to detect and respond to anomalous user behavior in real-time, enhancing security and mitigating the
risk of unauthorized access and data breaches.
Base-2’s data access management solution centers on safeguarding sensitive data assets by implementing
granular access controls and encryption mechanisms. We emphasize data classification and tagging to
ensure that information is appropriately categorized based on its sensitivity and regulatory
requirements. Additionally, data usage is closely monitored, and policies are enforced to prevent
unauthorized access, leakage, or misuse of critical data, thereby enhancing security and compliance
within the organization.
At Base-2, we provide clear and comprehensive presentations and reports of data-related insights and
trends. Our solution involves the use of intuitive and interactive visualizations to facilitate
understanding and decision-making among stakeholders. We use the latest technology like Splunk and
other visualization platforms to effectively communicate complex information, identify patterns, and
detect anomalies within datasets, thereby enhancing transparency, collaboration, and informed
decision-making across the enterprise.
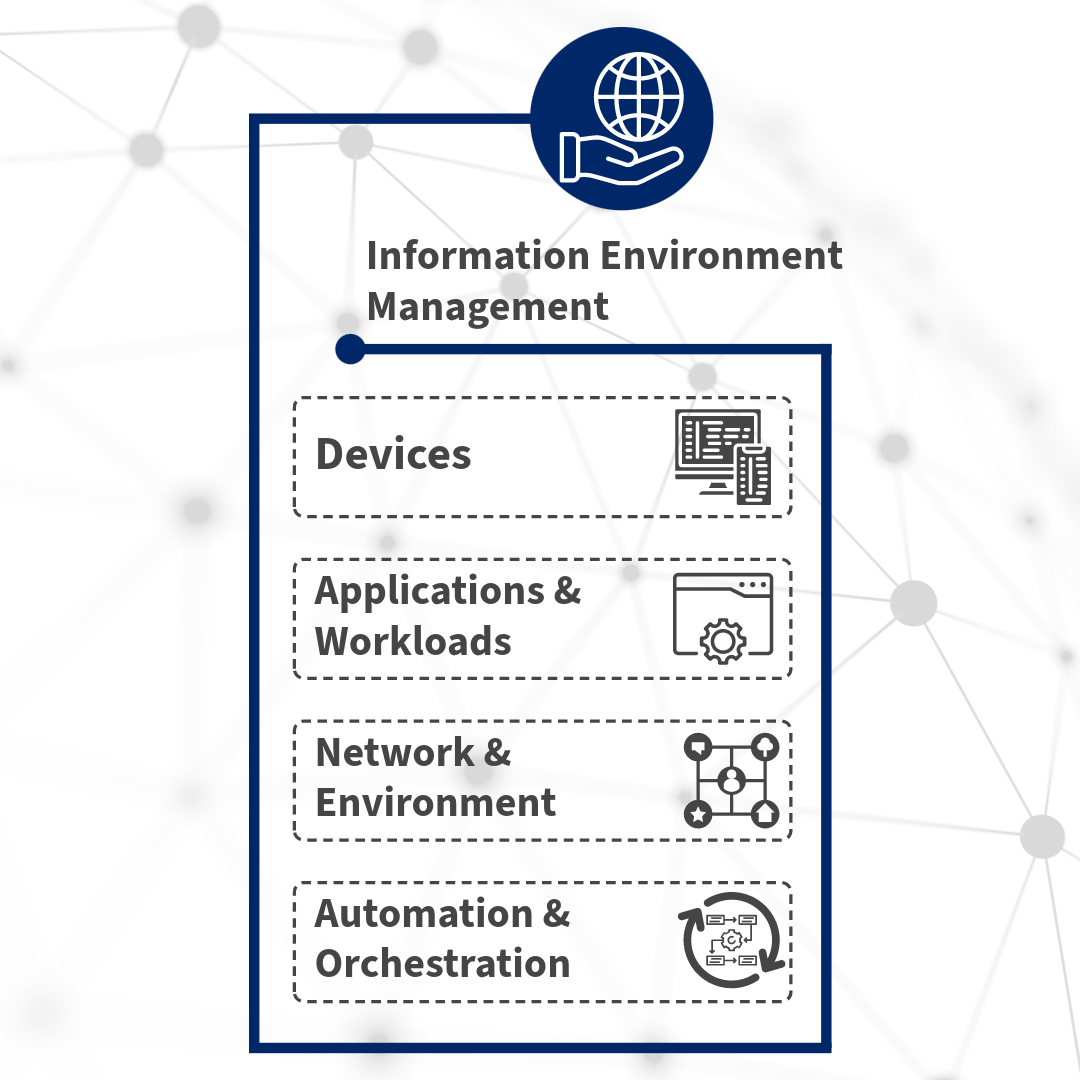
Information Environment Management
At Base-2, we ensure the security and integrity of devices seeking access to organizational resources.
Our solution involves implementing device identity verification, establishing trust based on device
health and compliance status, and enforcing policies to control device access to sensitive data and
applications. Additionally, we leverage continuous monitoring and risk assessment of devices help
detect and respond to security threats in real-time, enhancing overall security posture and mitigating
the risk of data breaches and unauthorized access.
Base-2’s Applications & Workloads solution emphasizes securing access to applications and workloads
regardless of their location, whether on-premises or in the cloud. We implement strict access
controls, least privilege principles, and micro-segmentation to limit lateral movement within a
network and reduce the attack surface. Additionally, continuous monitoring and real-time threat
detection mechanisms help identify and respond to potential security incidents, ensuring the integrity
and availability of critical applications and workloads while maintaining a robust security posture
across the organization.
Securing network infrastructure and surrounding environments is of chief importance to Base-2’s Zero
Trust solution. Our strategy includes implementing segmentation, encryption, and access controls to
isolate and protect sensitive assets from unauthorized access and lateral movement within the network.
Additionally, we employ continuous monitoring, threat intelligence, and anomaly detection techniques
to identify and respond to potential security threats in real-time, ensuring the integrity and
confidentiality of critical resources and data across the network infrastructure and environment.
Base-2’s Zero Trust solution enhances agility, scalability, and resilience in our customers’ security
operations while maintaining compliance and mitigating risks effectively. We leverage automated
processes and workflows to streamline security operations and response mechanisms. We save time
and money by automating routine tasks such as user authentication, access provisioning, and threat
detection, reducing manual intervention and minimizing human error. Additionally, our orchestration
capabilities enable the coordination of security controls and responses across diverse security tools
and platforms, ensuring a cohesive and effective defense posture against evolving cyber threats.